"Military", "Bank", and SSL Security Aren't what you think!

“Military Grade” or “Bank Grade” encryption doesn’t necessarily mean that your information is safe.
These claims are usually more marketing than security.
My name is Michael Lester. I’m the co-founder of IronClad Family, a certified information Security Manager, Certified Information Privacy Professional, and Certified Ethical Hacker, and teach ethical hacking and network security to master’s degree students at a U.S. university. I eat, breathe, sleep, and dream security! In this blog, I’m going to give you a high-level overview of why many website claims of “Military Grade”, “Bank Grade”, or “SSL” security don’t really protect your information and what you can do about it.
Almost every website claims to use some sort of “top-level encryption.” They throw out marketing terms that sound impressive like “Bank Grade Security”, “Military Grade Encryption”, “Encryption in Transit”, and “Encryption at Rest”.
Publishing claims like this is like a bus company proclaiming, “Our drivers all pass a rigorous exam and are licensed by the state.” Of course, they are! You and I know that to drive a bus you are required to have a license, but if you didn’t know that, then this claim might sound impressive. This is the current state of advertising and marketing around security.
SSL is Mandatory?
Here’s a little secret…If a website accepts any type of payment, then they ARE REQUIRED to use a technology called “SSL” and SSL uses an encryption algorithm called AES-256 which is a published common encryption algorithm that everyone uses, even the military. Because of this requirement, many companies claim “Bank Level Security” or “Military Grade Encryption.”
By that logic though, every company that takes payments online can claim that they use “Military Grade Encryption” and have “Bank Level Security.” So…“Momma’s Cookies” uses “Bank Level” encryption. “Aunt Martha’s Colonial Sewing Patterns” uses Bank Level encryption, and even “Chuck E. Cheese”, I guess, has “Bank Level Security.”
But let’s be serious…would you trust your most sensitive and important information to the Chuck E. Cheese restaurant chain? I hope not! Protecting information entails a lot more than just using an encryption algorithm that companies are required to use as an absolute minimum.
What is SSL anyway?
Let’s look at SSL. What is SSL anyway? SSL stands for “Secure Socket Layer” and is nothing more than a way to keep information confidential while it is being transmitted across the internet. Here is how it works:
The internet is made up of literally thousands and thousands of computers all networked together. Normally when you send something from one place to another on the internet, it passes through many different computers on its path from you to its destination.

Figure 1 - The Internet
Without any kind of encryption, the information you send is readable by everyone along the entire journey your data takes through the internet. If you see the address of a site start with http:// then you know they don’t use SSL and your data is not secure.

Figure 2 - Unencrypted, clear text through the Internet
SSL (Secure Socket Layer) creates a protected tunnel from the sending computer to the receiving computer so that no one can easily read your information on its electronic journey. Think of it like putting a letter in an envelope before sending it through the mail. No one can see what you wrote because it’s in the envelope all the way to the final recipient. This is called “Encryption in transit”, meaning the data is encrypted while it is being moved. Sites that start with https:// (note the “s”) are using SSL.

Figure 3 - Basic SSL
Why SSL isn’t enough.
Generally speaking, this works well, but there are two major problems. The first is a hack called Man-In-The-Middle, or MITM. Using this hack, a hacker breaks the SSL tunnel and inserts themselves in the middle. They receive information, look at it or possibly change it, then send it down the tunnel again. Neither the sender nor the receiver is any wiser. Using the same analogy as above, it is like someone opening your envelope, reading your letter, then putting it in another envelope and sending it on its way. This hack isn’t easy to do, but I personally demonstrate it to my classes. It is definitely possible.

Figure 4 - Man-In-The-Middle Attack
The other major problem with claiming that data is secure just because a company uses SSL is that your information might be secure from your computer to the destination computer, but once it gets to its destination it is once again completely readable by everyone at the destination. This might make sense if you are sending instructions to a bank because you trust the bank and want the various tellers and other employees to act on your instructions, but if you are sending sensitive, personal information, do you want it available to everyone that works at that company?
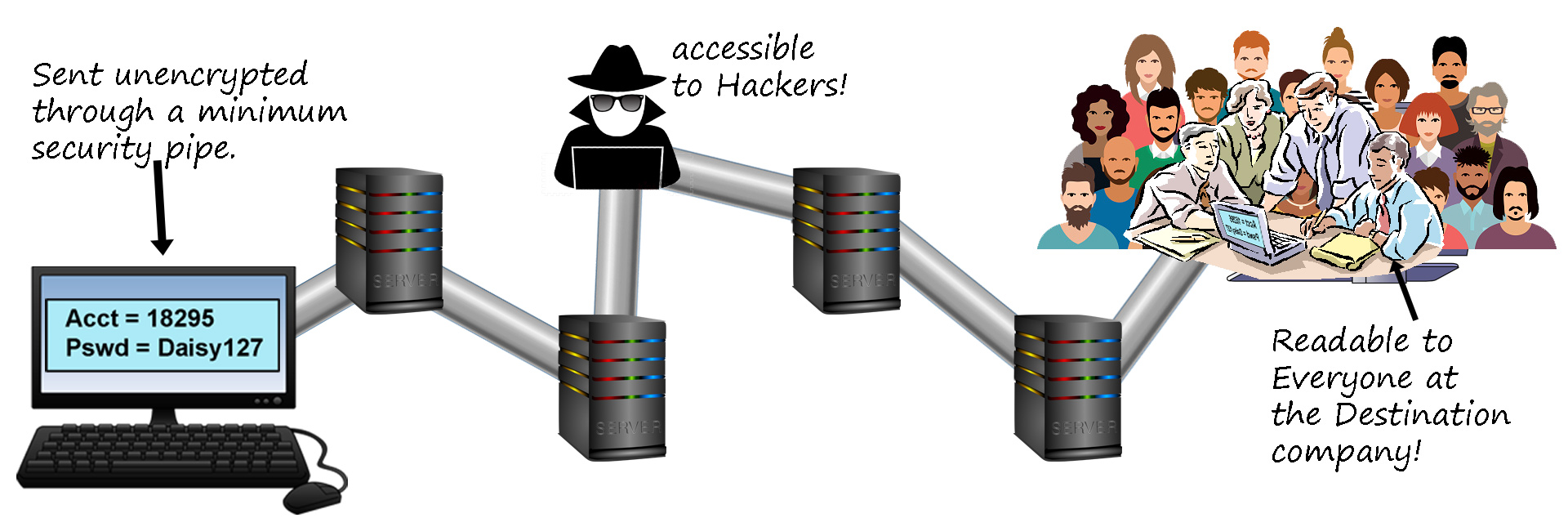
Figure 5 - SSL Doesn't protect your Information at the Destination.
Some companies try to address this glaring shortcoming in security by stating that they encrypt your information after receiving it. This is called “Encryption at Rest”, meaning that data is encrypted when it is just being stored. That’s great, but since they encrypted it, they can decrypt it. That just makes sense, right? That also means that since the company has the keys, a disgruntled employee could access the keys and decrypt them, or a hacker could, or it could be decrypted by mistake and then released to the public. A look at any week’s headlines will prove that this is A LOT more common than we’d like to believe.
Encrypting your information after it is received is like locking your information in a box with a lock to which someone else has the keys. They can also unlock it at any time, or the keys can be stolen and your information compromised.
From these examples, you can understand that HOW a company uses encryption is much more important than just the fact that they are using it.
The only guaranteed way to protect data..
The only way to truly protect your information is with something called “End-to-End Zero-Knowledge encryption”. Although that can sound complicated, the concept is very simple. It just means that your information is encrypted on your personal computer or phone BEFORE it is sent anywhere. That means that while it is being transmitted through the internet, and after it arrives at its destination, it is already fully encrypted and no one else can see it or decrypt it because they don’t have the keys! Keeping with our same analogy. It is like putting your information in a safe, locking the safe and keeping the keys, and then sending your safe to someone else to be stored. They can’t get in. Only you, or the person to whom you give your keys, can get in.
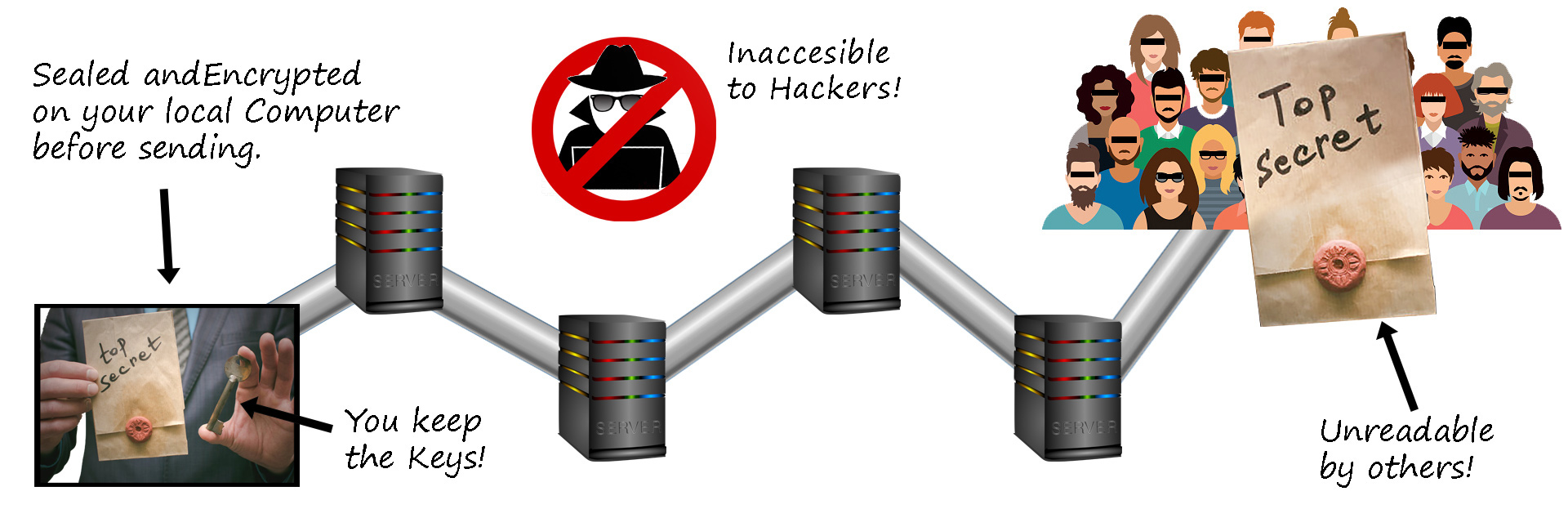
Figure 6 - End-To_End Zero-Knowledge Security
Why doesn’t everyone use End-to-End Zero-Knowledge Encryption?
You might ask, if this is the only way to keep information safe, why doesn’t everyone do that?
It’s a great question. The answer is, although the concept is easy, implementing End-To-End Zero-Knowledge encryption is technically difficult and costly. Most companies don’t want to take the time, effort, or cost, and figure that you, the user or consumer, don’t know any better and won’t care. They are more concerned with sales and marketing than they are with your actual data, that’s why they try to proclaim they have “Bank Level Security” just because they use mandated minimum tools.
Once you understand the risk of not using End-to-End Zero-Knowledge encryption, and how insecure your information is when you don’t, why would anyone trust their important information to any company that doesn’t want to take the time and effort to truly protect it? I know I wouldn’t!
The only company that uses End-to-End Zero-Knowledge Encryption
After explaining all of this, it shouldn’t come as a surprise that the IronClad Family took the time and made the investment to implement End-to-End Zero-Knowledge encryption. In fact, we are the ONLY online personal information protection service that has! It hasn’t been easy. It took us three years to figure out how to implement computer code so that a client’s information could be fully protected, but still accessible to designated recipients if something happened to that client. Most of our competitors haven’t even been in business that long.
I told you at the beginning of this article that I eat, breathe, sleep, and dream security, but that is only partially true. Our whole team does too! Together, we form the philosophy and culture of the IronClad Family, so to be fully correct, I should state that the IronClad Family eats, breathes, sleeps, and dreams security, and I should add that we sleep well because we know that all of our client’s personal information is fully encrypted, End-to-End, and we don’t have to worry.
Be Ready. Be safe.

